Table of Contents
Hash functions form the very basis of modern cryptography and are core to the architecture of Web3 technologies. This technical deep dive will explain the intricacies of hash functions, their implementation in Web3, and their crucial role in shaping the future of decentralized systems.
Introduction to Hash Functions
A hash function, on the other hand, is fundamentally a mathematical algorithm that transforms an arbitrary-sized input into a fixed-size output. The deterministic nature of hash functions ensures that identical inputs always produce identical outputs, while their collision resistance makes it computationally infeasible to find two different inputs that generate the same hash value.
One-way cryptographic hash functions mean that the computation of a hash value from input data is computationally easy, while deriving the original input from the hash value alone is computationally infeasible. This property is called pre-image resistance and is one of the main factors securing sensitive information and maintaining the integrity of blockchain networks.
Hash Functions in the Web3 Ecosystem
Hash functions are foundational in almost any cryptographic operation or mechanism that occurs in the scope of Web3. Starting with the generation of unique identifiers either for a transaction or blocks to securing the very integrity of an entire blockchain network through digital signatures, the role of robust cryptographic primitives independent from central authority oversight is something with which hash functions comfortably fit most such security-critical operations within this class of highly decentralized applications.
In dApps, hash functions are in wide usage, allowing for secure user authentication, verification of data, and processing of transactions. They’re particularly crucial in maintaining the immutability of blockchain records and ensuring the consistency of distributed ledger states across network nodes.
Common Hash Functions in Web3
A few hash functions have become standards in the Web3 ecosystem, each rooted in different mathematics and providing different security properties. Let’s examine how some of these key algorithms work on the inside.
SHA-256 (Secure Hash Algorithm 256-bit)
SHA-256 falls under the SHA-2 family and runs on messages in serial mode. It uses very complicated mathematical operations. The procedure of the algorithm involves the following major steps:
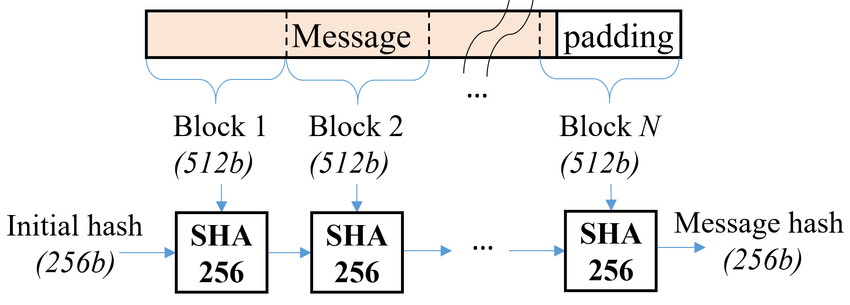
- Message Padding: The input message M is padded to ensure its length is a multiple of 512 bits. This involves:
- Append a single ‘1’ bit
- Add k ‘0’ bits, where k is the smallest non-negative solution to: l + 1 + k ≡ 448 mod 512
- Append the original message length l as a 64-bit big-endian integer
2. Message Schedule Creation: The padded message is divided into 512-bit blocks (M₁, M₂, …, Mₙ). For each block:
- Split into 16 32-bit words (W₀, W₁, …, W₁₅)
- Extend to 64 words using the formula:
Wᵢ = σ₁(Wᵢ₋₂) + Wᵢ₋₇ + σ₀(Wᵢ₋₁₅) + Wᵢ₋₁₆
where σ₀(x) = ROTR⁷(x) ⊕ ROTR¹⁸(x) ⊕ SHR³(x)
and σ₁(x) = ROTR¹⁷(x) ⊕ ROTR¹⁹(x) ⊕ SHR¹⁰(x)
3. Compression Function: It Uses eight working variables (a, b, c, d, e, f, g, h) initialized with the first 32 bits of the fractional parts of the square roots of the first 8 primes.
The main compression loop: For i from 0 to 63:
T₁ = h + Σ₁(e) + Ch(e,f,g) + Kᵢ + Wᵢ
T₂ = Σ₀(a) + Maj(a,b,c)
h = g
g = f
f = e
e = d + T₁
d = c
c = b
b = a
a = T₁ + T₂ where:
Σ₀(x) = ROTR²(x) ⊕ ROTR¹³(x) ⊕ ROTR²²(x)
Σ₁(x) = ROTR⁶(x) ⊕ ROTR¹¹(x) ⊕ ROTR²⁵(x)
Ch(x,y,z) = (x ∧ y) ⊕ (¬x ∧ z)
Maj(x,y,z) = (x ∧ y) ⊕ (x ∧ z) ⊕ (y ∧ z)Keccak-256 (Ethereum’s Hash Function)
Keccak-256, used in Ethereum, follows quite a different approach than the traditional one called the sponge construction. Its mathematical structure consists of:
- State Array: A 5×5×64 state array of bits, adding up to a total of 1600 bits
- Round Function f:
Composed of five steps (θ, ρ, π, χ, ι): θ step: C[x] = A[x,0] ⊕ A[x,1] ⊕ A[x,2] ⊕ A[x,3] ⊕ A[x,4]
D[x] = C[x-1] ⊕ ROT(C[x+1], 1)
A[x,y] = A[x,y] ⊕ D[x] ρ and π steps: B[y,2x+3y] = ROT(A[x,y], r[x,y]) χ step: A[x,y] = B[x,y] ⊕ ((¬B[x+1,y]) ∧ B[x+2,y]) ι step: A[0,0] = A[0,0] ⊕ RC
where RC is a round constant and ROT represents bitwise rotation.
- Absorption Phase: The input message is padded and divided into r-bit blocks (r=1088 for Keccak-256), which are XORed into the first r bits of the state
- Squeezing Phase: The first r bits of the state are output, and the state is permuted using f between each output block until the desired output length is reached
RIPEMD-160
RIPEMD-160 uses a dual-stream compression function with parallel computations:
- Message Block Processing:
For each 512-bit message block Mᵢ:
- Split into 16 32-bit words x₀, x₁, …, x₁₅
- Process through two parallel lines (left and right)
- Each line performs 80 steps using different constants and functions
- Compression Function:
h(H,M) = H + (h'(H,M) ≫ s) + (h”(H,M) ≫ s’)
where h’ and h” are the left and right line outputs
and s, s’ are fixed rotations - Step Function:
A = (A + f(j,B,C,D) + Xᵢ + K(j)) ≪ s
where f(j,X,Y,Z) varies for different step ranges:
- Steps 0-15: f(X,Y,Z) = X ⊕ Y ⊕ Z
- Steps 16-31: f(X,Y,Z) = (X ∧ Y) ∨ (¬X ∧ Z)
- Steps 32-47: f(X,Y,Z) = (X ∨ ¬Y) ⊕ Z
- Steps 48-63: f(X,Y,Z) = (X ∧ Z) ∨ (Y ∧ ¬Z)
- Steps 64-79: f(X,Y,Z) = X ⊕ (Y ∨ ¬Z)
The combined usage of all of these hash functions within Web3 protocols demonstrates a proper choice based on the needed security and/or performance constraints. For example, Bitcoin uses SHA-256 combined with RIPEMD-160 to generate the addresses in its protocol, aiming to balance both security and efficiency, while Ethereum chose Keccak-256 since it could efficiently be implemented in smart contracts, featuring resistance to length extension attacks.
Implementation Examples
Let’s examine practical implementations of these hash functions:
Implementation of SHA-256
class SHA256 {
constructor() {
this.h = new Uint32Array([
0x6a09e667, 0xbb67ae85, 0x3c6ef372, 0xa54ff53a,
0x510e527f, 0x9b05688c, 0x1f83d9ab, 0x5be0cd19
]);
this.k = new Uint32Array([
0x428a2f98, 0x71374491, 0xb5c0fbcf, 0xe9b5dba5,
// ... (remaining constants)
]);
}
// Right rotate function
rotr(n, x) {
return (x >>> n) | (x << (32 - n));
}
// SHA-256 functions
Ch(x, y, z) { return (x & y) ^ (~x & z); }
Maj(x, y, z) { return (x & y) ^ (x & z) ^ (y & z); }
Σ0(x) { return this.rotr(2, x) ^ this.rotr(13, x) ^ this.rotr(22, x); }
Σ1(x) { return this.rotr(6, x) ^ this.rotr(11, x) ^ this.rotr(25, x); }
σ0(x) { return this.rotr(7, x) ^ this.rotr(18, x) ^ (x >>> 3); }
σ1(x) { return this.rotr(17, x) ^ this.rotr(19, x) ^ (x >>> 10); }
// Process a 512-bit block
processBlock(M) {
const W = new Uint32Array(64);
// Message schedule
for (let t = 0; t < 16; t++) {
W[t] = M[t];
}
for (let t = 16; t < 64; t++) {
W[t] = this.σ1(W[t-2]) + W[t-7] + this.σ0(W[t-15]) + W[t-16];
}
// Working variables
let [a, b, c, d, e, f, g, h] = this.h;
// Main loop
for (let t = 0; t < 64; t++) {
const T1 = h + this.Σ1(e) + this.Ch(e, f, g) + this.k[t] + W[t];
const T2 = this.Σ0(a) + this.Maj(a, b, c);
[h, g, f, e, d, c, b, a] = [g, f, e, d + T1, c, b, a, T1 + T2];
}
// Update hash values
this.h = this.h.map((x, i) => x + [a, b, c, d, e, f, g, h][i]);
}
}Keccak-256 Implementation Example
class Keccak {
constructor() {
this.state = new Uint8Array(200); // 1600 bits
this.rate = 1088 / 8; // Rate in bytes
}
// Keccak-f[1600] permutation
keccakF() {
const rounds = 24;
const rotationConstants = [
[0, 1, 62, 28, 27],
[36, 44, 6, 55, 20],
[3, 10, 43, 25, 39],
[41, 45, 15, 21, 8],
[18, 2, 61, 56, 14]
];
for (let round = 0; round < rounds; round++) {
// θ step
const C = new Array(5);
const D = new Array(5);
for (let x = 0; x < 5; x++) {
C[x] = this.state[x] ^ this.state[x + 5] ^
this.state[x + 10] ^ this.state[x + 15] ^
this.state[x + 20];
}
for (let x = 0; x < 5; x++) {
D[x] = C[(x + 4) % 5] ^ this.rotateLeft(C[(x + 1) % 5], 1);
for (let y = 0; y < 5; y++) {
this.state[x + 5 * y] ^= D[x];
}
}
// ρ and π steps combined
let current = this.state[1];
for (let x = 0; x < 5; x++) {
for (let y = 0; y < 5; y++) {
const newX = y;
const newY = (2 * x + 3 * y) % 5;
const offset = rotationConstants[x][y];
const temp = this.state[newX + 5 * newY];
this.state[newX + 5 * newY] = this.rotateLeft(current, offset);
current = temp;
}
}
// χ step
for (let y = 0; y < 5; y++) {
const T = new Array(5);
for (let x = 0; x < 5; x++) {
T[x] = this.state[x + 5 * y];
}
for (let x = 0; x < 5; x++) {
this.state[x + 5 * y] = T[x] ^
((~T[(x + 1) % 5]) & T[(x + 2) % 5]);
}
}
// ι step
this.state[0] ^= this.roundConstants[round];
}
}
}RIPEMD-160 Implementation Example
class RIPEMD160 {
constructor() {
this.h = new Uint32Array([
0x67452301, 0xefcdab89, 0x98badcfe, 0x10325476, 0xc3d2e1f0
]);
}
// The five basic functions
f1(x, y, z) { return x ^ y ^ z; }
f2(x, y, z) { return (x & y) | (~x & z); }
f3(x, y, z) { return (x | ~y) ^ z; }
f4(x, y, z) { return (x & z) | (y & ~z); }
f5(x, y, z) { return x ^ (y | ~z); }
// Process a block
processBlock(block) {
let [a1, b1, c1, d1, e1] = this.h;
let [a2, b2, c2, d2, e2] = this.h;
// Left line
for (let j = 0; j < 80; j++) {
let T = this.rotateLeft(
a1 + this.f(j, b1, c1, d1) + block[this.r1[j]] + this.K1(j),
this.s1[j]
) + e1;
[a1, b1, c1, d1, e1] = [e1, T, b1, this.rotateLeft(c1, 10), d1];
}
// Right line
for (let j = 0; j < 80; j++) {
let T = this.rotateLeft(
a2 + this.f(79-j, b2, c2, d2) + block[this.r2[j]] + this.K2(j),
this.s2[j]
) + e2;
[a2, b2, c2, d2, e2] = [e2, T, b2, this.rotateLeft(c2, 10), d2];
}
// Combine results
let T = this.h[1] + c1 + d2;
this.h[1] = this.h[2] + d1 + e2;
this.h[2] = this.h[3] + e1 + a2;
this.h[3] = this.h[4] + a1 + b2;
this.h[4] = this.h[0] + b1 + c2;
this.h[0] = T;
}
}The following implementations below outline the internal details of each hash function, but in a real-world application, it is always advisable to use well-tested cryptography libraries instead of any self-made implementation of these functions. Below code snippets just illustrate the above-mentioned mathematical operations and transformations and provide a more concrete reference for how these algorithms work.
Hashing in Blockchain Protocols
Hashing plays a much greater role in blockchain protocols than providing basic integrity. In proof-of-work consensus algorithms, miners have to find a nonce such that, combined with block data, the hash value of this combination meets certain criteria, usually a certain number of starting zero bits. This computational challenge provides security for the network, as through this approach the resource costs associated with creating blocks become prohibitively costly.
Hash functions play a significant role in digital signatures within blockchain transactions. While creating a transaction, it is the hash of the transaction data that gets signed by the sender’s private key, not the complete transaction. This ensures data integrity while reducing computational overhead during signature operations.
Merkle trees, fundameMerkle trees are a common component of blockchain architectures. They implement hash functions with the key property of providing efficient proofs of inclusion of data. In a Merkle tree, every non-leaf node contains a hash of the concatenated values of its child nodes, converging into a single root hash that summarizes a set of transactions in a block.
Smart Contracts and Hash Functions
Smart contracts leverage hash functions in numerous ways to ensure secure and verifiable execution of programmatic agreements. Random number generation in smart contracts often involves combining multiple sources of entropy with hash functions to create unpredictable yet verifiable results. This approach is crucial for applications like gambling dApps or random prize distributions.
Cryptographic commitments in smart contracts frequently use hash functions to allow parties to commit to a value without revealing it immediately. For example, in a blockchain-based voting system, voters might first submit the hash of their vote, later revealing the actual vote during the counting phase. The hash commitment ensures votes cannot be changed while maintaining privacy during the voting period.
Zero-knowledge proofs, increasingly important in privacy-preserving smart contracts, rely heavily on hash functions for creating succinct proofs of computation. These proofs allow one party to prove they know certain information without revealing the information itself, a capability essential for maintaining privacy in transparent blockchain systems.
Security Considerations and Challenges
While hash functions provide robust security guarantees, their implementation in Web3 systems presents unique challenges. Hash collision attacks, though theoretically possible, become practically infeasible with properly chosen hash functions and output sizes. However, the increasing power of quantum computers poses a potential threat to current hash function security, particularly regarding collision resistance.
Pre-image attacks, where an attacker attempts to find an input that produces a specific hash value, remain a concern for certain applications. Smart contract developers must be particularly careful when using hash functions for random number generation or commitment schemes, as predictable inputs could lead to exploitable patterns.
To mitigate these risks, Web3 protocols often implement additional security measures alongside hash functions. These might include using multiple hash functions in combination, adding salt values to inputs, or implementing time-delay mechanisms to prevent certain types of attacks.
Use Cases and Real-world Applications
The practical applications of hash functions in Web3 extend across numerous projects and platforms. Bitcoin’s use of double SHA-256 hashing in its proof-of-work system has demonstrated the resilience of well-implemented hash functions at scale. Ethereum’s account model relies on Keccak-256 for address generation and transaction verification, processing millions of operations daily.
InterPlanetary File System (IPFS) uses content-based addressing through hash functions to create unique identifiers for stored files. This approach enables efficient content distribution and verification across decentralized networks. Similarly, Git version control systems use SHA-1 (though transitioning to SHA-256) for commit identification and integrity verification.
Future of Hashing in Web3
The evolution of Web3 technologies continues to push the boundaries of hash function applications. Emerging consensus mechanisms like proof-of-stake still rely on hash functions for block production and validation, though in different ways than traditional proof-of-work systems. Privacy-focused protocols are exploring novel applications of hash functions in zero-knowledge proofs and other privacy-preserving mechanisms.
The potential impact of quantum computing has sparked research into quantum-resistant hash functions and hybrid cryptographic systems. These developments suggest that while the fundamental importance of hash functions in Web3 will persist, their implementation and usage patterns may evolve significantly.
As Web3 continues to mature, we can expect to see new applications of hash functions in areas like decentralized identity systems, cross-chain bridges, and layer-2 scaling solutions. The challenge will be maintaining security and efficiency while adapting to emerging threats and technological advances.
Conclusion
Hash functions remain central to the security and functionality of Web3 systems, from basic transaction verification to complex privacy-preserving protocols. Understanding their properties, implementations, and limitations is crucial for developers and architects working in the Web3 space. As the ecosystem evolves, hash functions will continue to adapt and find new applications in securing and enabling decentralized systems. If you are interested to know more about the Cryptographic Hash Functions you can learn it through this detailed course by IBM.