Table of Contents
Ever wondered how Bitcoin verifies a transaction without downloading the entire blockchain, or how, in peer-to-peer networks, file integrity is ensured when portions of it are downloaded from different sources? The answer involves a really smart data structure known as a Merkle Tree. In this post, we’ll see Merkle Trees from the ground up and understand not just what they are but why they’re so important in modern technology.
Why Do We Need Merkle Trees?
Suppose you are downloading some big file, such as a movie or game, from the Internet. You have no guarantee that what was downloaded is precisely what you got. You might even suspect that someone tampered with it en route. This is what Merkle Trees ensures.
This problem becomes even more critical in blockchain systems such as Bitcoin. You might want to verify that your transaction was in one block without downloading the whole blockchain, which is hundreds of gigabytes in size. Merkle Trees allows you to do just that and ensure data integrity efficiently.
Understanding Merkle Trees: Starting with the Basics
What is a Merkle Tree?
A Merkle Tree is like a family tree for data. Just as a family tree shows how everyone is connected, a Merkle Tree shows via the “fingerprints” or cryptographic hashes of the data how pieces of data are related. Let’s break this down step by step.
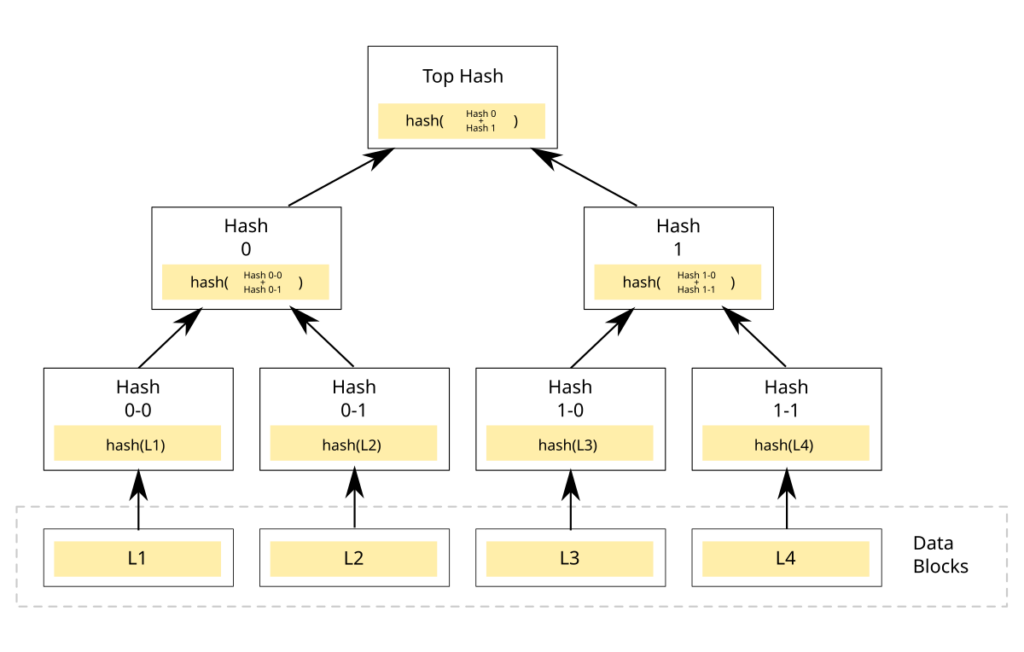
The Building Blocks
- Data Blocks: These are the chunks of information you want to validate; in Bitcoin, these are transactions, but they might be pieces of the file in some sort of file-sharing scenario.
- Hash Functions: You can think of these as fingerprint machines: they take any input, say a transaction, and produce a fixed-size output, the fingerprint that identifies that input uniquely. If you change even one tiny bit of the input, the fingerprint changes completely.
- Tree Structure: A tree is formed by arranging those fingerprints in such a way that all the data sits at the very bottom, then combines the fingerprints as we move upwards.
Building a Merkle Tree: A Simple Example
Let’s build a Merkle Tree with four transactions (Tx1, Tx2, Tx3, and Tx4). Here’s how it works:
- First Level (Leaf Nodes):
- Take each transaction and create its hash (fingerprint)
- Hash of (Tx1) = H1
- Hash of (Tx2) = H2
- Hash of (Tx3) = H3
- Hash of (Tx4) = H4
- Second Level:
- Combine pairs of hashes and hash them together
- Hash of (H1 + H2) = H12
- Hash of (H3 + H4) = H34
- Final Level (Root):
- Combine the last pair to get the Merkle Root
- Hash of (H12 + H34) = Root Hash
This root hash is special because it represents all the data beneath it. If any transaction changes, the root hash will also change.
Merkle Proofs: The Magic of Verification
Here’s where Merkle Trees get interesting. Let’s say you want to prove that Tx2 is part of this tree without showing all the transactions. You only need three pieces of information:
- The transaction (Tx2)
- Hash1 (to combine with Hash2)
- Hash34 (to combine with Hash12)
With just these pieces, anyone can:
- Calculate Hash2 from Tx2
- Combine Hash2 with Hash1 to get Hash12
- Combine Hash12 with Hash34 to get the Root Hash
If this calculated root matches the known root hash, the transaction is verified! This is called a Merkle Proof.
Real-World Applications
Bitcoin and Cryptocurrencies
Bitcoin uses Merkle Trees in every block of transactions, especially in the implementation of Simple Payment Verification (SPV). When you use a lightweight wallet (like on your phone), it doesn’t download the whole blockchain. Instead, it:
- Downloads just the block headers (which contain Merkle roots)
- Gets Merkle proofs for your transactions
- Verifies that your transactions are included without needing the other thousands of transactions in each block
File Sharing Systems
When you download a large file through BitTorrent or IPFS:
- The system divides the file into pieces
- Creates a Merkle Tree of all pieces
- As you download each piece from different sources, you can verify it’s correct using Merkle proofs
- If any piece is corrupted or tampered with, you’ll know immediately
Advantages of Merkle Trees
- Efficiency: You only need a small amount of data to verify that something is part of a larger set
- Security: It’s practically impossible to fake a Merkle-proof
- Space Saving: Light clients (like mobile wallets) can work without downloading everything
Limitations to Consider
- Initial Computation: Building the tree requires calculating many hashes
- Updates: If data changes, you need to recalculate parts of the tree
- Proof Size: While efficient, proofs get slightly larger as the tree gets bigger
Advanced Concepts Made Simple
Sparse Merkle Trees
Imagine a Merkle Tree with slots for every possible piece of data, even if most slots are empty. This is a Sparse Merkle Tree. It’s like having a huge library with mostly empty shelves but being able to quickly prove whether a book exists or not.
Merkle Patricia Trees
Used in Ethereum, these are like Merkle Trees with a better filing system. They make it easier to track accounts and their balances, like a super-efficient filing cabinet that can prove what’s inside any drawer.
Implementing Your Own Merkle Tree
Here’s a simple Python implementation for Merkle Tree. If you want to get an in-depth idea of the implementation, read the blog: “Merkle Tree: A Simple Explanation and Implementation.”
import hashlib
class MerkleTree:
def __init__(self, data_blocks):
self.leaves = [self.hash_data(block) for block in data_blocks]
self.root = self.build_tree(self.leaves)
def hash_data(self, data):
return hashlib.sha256(str(data).encode()).hexdigest()
def build_tree(self, leaves):
if len(leaves) == 1:
return leaves[0]
new_level = []
for i in range(0, len(leaves), 2):
if i + 1 < len(leaves):
new_hash = self.hash_data(leaves[i] + leaves[i+1])
else:
new_hash = leaves[i] # Duplicate last node if odd
new_level.append(new_hash)
return self.build_tree(new_level)
# Example usage
transactions = ["Tx1", "Tx2", "Tx3", "Tx4"]
tree = MerkleTree(transactions)
print(f"Merkle Root: {tree.root}")Conclusion
Merkle Trees are an intelligent solution to one complex problem: ensuring data integrity is effectively achieved in a distributed system. From Bitcoin to even downloading a file or building up your system, the concept of a Merkle Tree provides a way to understand how most modern digital systems maintain trust with efficiency.
If you want to understand more of the details, try to implement the simple Merkle Tree above and play with different data sets. Once you feel comfortable with the basics, you can then go ahead to understand some more advanced versions, such as Sparse Merkle Trees, or study how Bitcoin and Ethereum use these structures in their protocols.
Remember, every complex system is built on simple principles combined in clever ways. Merkle Trees are a perfect example of this—nothing but a combination of multiple simple hash.