Table of Contents
Introduction
Zero-knowledge proofs is a cryptography method that involves two parties a Prover and a Verifier. As the name suggests, the prover provides proof to another party, and the party that verifies the proof is the verifier. Now what is so different about proof verification here is that we had to build an entire subsection called the Zero-knowledge Proofs. Zero-knowledge here gives a bit of a hint, in short, we try to prove that a statement is true without revealing any relevant information about the statement.
Zero-knowledge proofs plays a crucial role in those applications where privacy, security, and efficiency are considered, such as blockchain technology and secure communication systems. We have two kinds of Zero-knowledge Proofs – zk snarks and zk starks, which stands for Zero-Knowledge Succinct Non-Interactive Argument of Knowledge, and Zero-Knowledge Scalable Transparent Argument of Knowledge respectively. They are succinct-proof, small, and fast to verify; non-interactive-few rounds of communication are needed between the prover and verifier; and the prover’s arguments know what they claim to know.
Basics of Zero-Knowledge Proof (ZKP)
Zero-knowledge proofs are based on three central properties: completeness, soundness, and the zero-knowledge property.
- Completeness guarantees that if a statement is true, the verifier will always accept proof by an honest prover.
- Soundness ensures that no cheating prover can convince a verifier of a false statement.
- Zero-knowledge property guarantees that the verifier does not learn anything about the underlying information beyond the fact that it is valid.
A very simple example of Zero-knowledge proofs is the so-called “Ali Baba Cave”: a prover demonstrates the knowledge of a secret passcode that opens some hidden door inside a cave without actually disclosing the passcode. This would convince the verifier of the knowledge, as he saw the prover disappear into the cave and then return to the starting point without learning the secret.
zkSNARKs: A Specialized Form of ZKP
zkSNARKs are a special form of Zero-knowledge proofs that extend these principles into new properties: succinctness allows proofs to remain small and verifiable in minimal time; non-interactivity allows the interaction between prover and verifier to be reduced to one round; finally, with zkSNARKs, it is ensured that the prover knows what he or she claims to know-that is, the Argument of Knowledge property.
These prove to be useful when multiple verifiers need proof so that there’s no need of multiple interactions between the prover and the verifier. For example: When rollups send transaction proof to the blockchain, since we have multiple miners needing the proof, SNARKs tend to be useful as they are short and fast and miners do not have to wait very long to receive the proof.
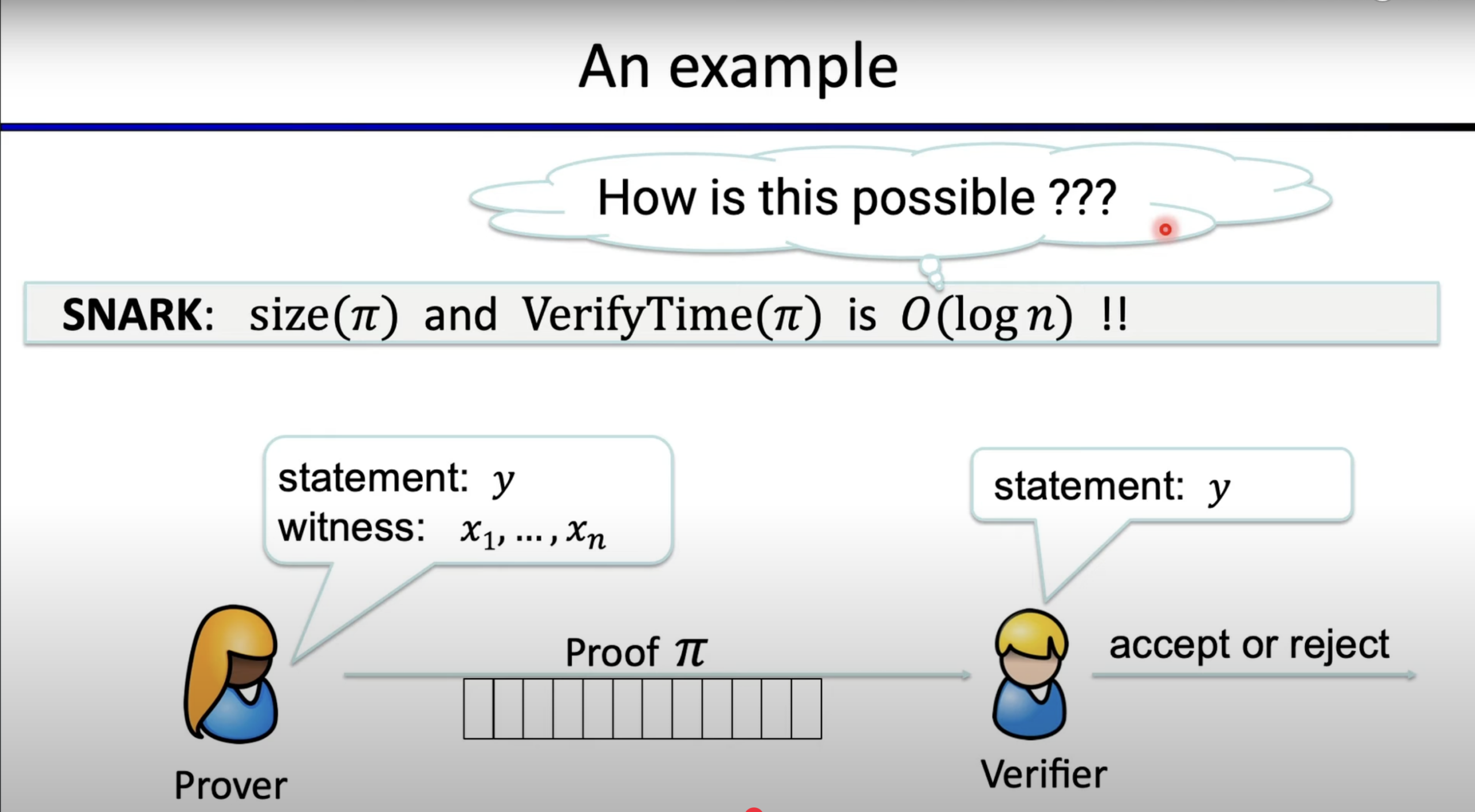
The general workflow of zkSNARK consists of three phases: Setup, proof generation, and verification. During the setup phase, some public parameters are generated via a trusted setup that will later be used in proof generation and verification. In the proof generation phase, the prover needs to use his secret knowledge along with the public parameters to generate proof. Finally, the verification phase allows the verifier to verify the validity of the proof without any further information on the underlying data.
Applications of zkSNARKs
The applications of zk snarks are immense specially everywhere we talk about Scalability, Privacy and Compliance. First, privacy-centric cryptocurrencies, such as Zcash, use zk snarks to shield transactions. By this, all information about either the sender or the recipient and the value transacted becomes hidden but without losing the capacity for proving its validity. Also these help us to have private transactions on public blockchains like Aleo.
Besides, these technologies enhance blockchain scaling by compressing transaction proofs. This allows for faster and seamless operations for example Snark Rollups which generate a faster proof and only require a single interaction between the Prover and the Verifier. Computational costs are decreased by offloading complex verification processes from the blockchain. For compliance category it proves helpful while proving solvency.
In the case of identity verification, for instance, zkSNARKs provide a secure way to prove attributes like age or membership status without revealing extraneous information. For example, one may prove eligibility to access some services instead of releasing his personal information.
Another critical application is within secure voting mechanisms. zk snark assure the validity of votes, without disclosing the identity of the voters or their choices, thus balancing openness with secrecy. Similarly, zk snark enables privacy-preserving data sharing even in sensitive domains such as health care, where patients can prove their eligibility for a service without revealing their entire medical history.
Real-World Examples and Implementations
Probably the most well-known usage of zk snarks is within Zcash, a privacy cryptocurrency. It leverages zkSNARKs in making shielded transactions that obscure critical transaction details while proving their validity to the network. Thus, it makes sure that privacy and transparency go hand in hand.
Ethereum, the second-largest blockchain, has also moved in the direction of implementing zkSNARKs to help its scalability and privacy. Solutions like zkSync and Starknet employ zkSNARKs for verification of computation performed off-chain, reducing the load on the Ethereum mainnet manifold. This allows increasing the throughput of transactions without losing security.
Learn to build a Decentralized Music Streaming and Tipping Platform on ZKsync by taking our course.
Other notable projects that have put zkSNARKs into application include Filecoin, which deploys them to prove replication on its storage network, and the Mina Protocol, a lightweight blockchain design relying heavily on the technology.
Benefits and Drawbacks of zkSNARK
zk snarks offer significant advantages. They enhance scalability by reducing computational and storage demands, enabling faster and cheaper transactions. Their privacy-preserving nature ensures secure verification without revealing sensitive data. Additionally, zkSNARKs provide efficient verification, making them suitable for complex computations.
However, zkSNARKs have their challenges. The trusted setup during initialization may introduce some vulnerability points whereby compromised parameters could undermine the security of the system. Proof generation is very resource-intensive and computationally intensive. Their security relies on complex cryptographic assumptions, too, which need further research and scrutiny.
Future of Zero-knowledge Proofs and zkSNARKs
The future of zkSNARKs is bright, and it has evolved into a new technology called zkSTARKs that does away with many limitations, including trusted setup. Researchers continue to improve the efficiency, scalability, and usability of zk snarks. Besides blockchain, other fields in which tSNARKs are potential game changers include secure communication and privacy-preserving machine learning. Once mature, such technologies will surely spread across non-blockchain domains.
In Web3 and DeFi, zkSNARKs are instrumental in enabling privacy-preserving financial transactions, secure identity management, and efficient contract verification. Their integration is positioned to be one of the major contributing section of the decentralized internet in ways yet to be figure as the web3 ecosystem is still in its early stages undergoing rapid development.
Conclusion
The ever-growing use of Zero-Knowledge Proof and zk snarks points to a far-sighted move toward practical realization of privacy, scalability, and security across many spheres: from blockchain technologies to enabling secure data sharing, zk snark enables modern cryptographic challenges to find a potent solution. With increased research and development, the way we view privacy and confidence in the digital world seems to have changed for sure.
