Table of Contents
As Web3 evolves rapidly, security and privacy continue to be among the primary concerns for developers, users, and enterprises alike. Trusted Execution Environments (TEEs) have recently been one of the great answers to these problems: they provide a secure environment in which sensitive computations and data processing may be safely processed without having the need to distribute information on decentralized systems. The following article will introduce basic principles about TEEs, applications in Web3, and the ecosystems built upon them.
Understanding Trusted Execution Environments
A Trusted Execution Environment is a secure area within a processor that guarantees code and data loaded inside will be protected with respect to confidentiality and integrity. Think of it as a fortress within your computer’s processor, where sensitive operations can be performed in isolation from the rest of the system.
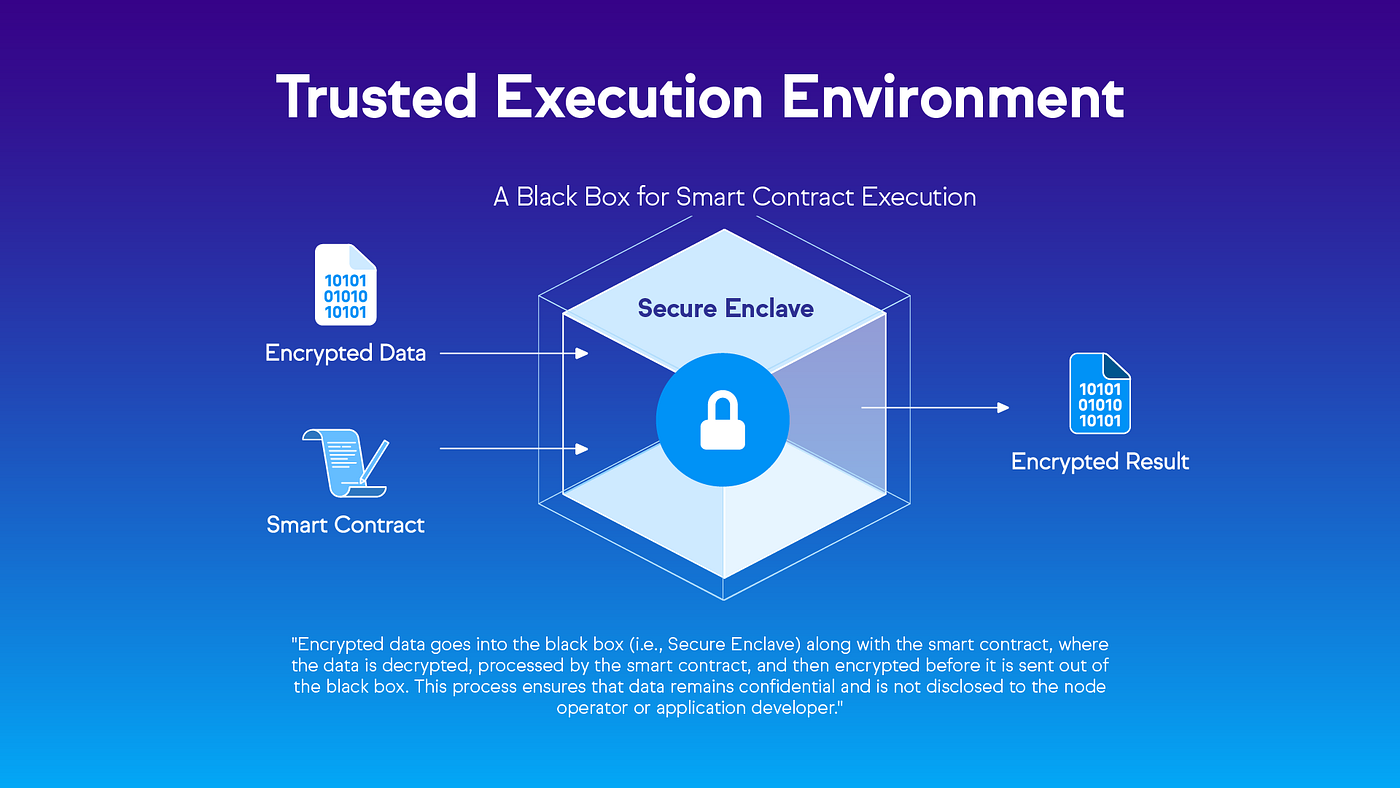
Key characteristics of Trusted Execution Environments (TEEs) include:
- Isolation: Code and data inside a Trusted Execution Environments (TEEs) are protected from access by other applications, the operating system, and even system administrators
- Integrity: The system can verify that the code running inside the Trusted-Execution-Environments(TEEs) hasn’t been tampered with
- Confidentiality: Data processed within the TEE remains encrypted and protected from external observation
- Attestation: The ability to prove to remote parties that a specific piece of code is running in a genuine rusted Execution Environments (TEEs)
TEE Technologies in Web3
Several TEE implementations are currently being utilized in the Web3 space:
Intel SGX (Software Guard Extensions)
Intel SGX is perhaps the most widely adopted TEE technology in Web3. It creates “enclaves” – protected regions of memory where sensitive computations can occur. Projects like Secret Network and Oasis Network have built their privacy-preserving blockchain solutions using Intel SGX.
ARM TrustZone
ARM’s TrustZone technology provides a secure execution environment for mobile and embedded devices. While less common in current Web3 applications, its potential for mobile-first blockchain applications is significant.
AMD SEV (Secure Encrypted Virtualization)
AMD’s offering provides memory encryption for virtual machines, making it particularly relevant for cloud-based blockchain infrastructure.
Use Cases in Web3
1. Privacy-Preserving Smart Contracts
One of the most promising applications of TEEs in Web3 is enabling confidential smart contract execution. Traditional blockchain transactions are fundamentally transparent, with all data and computations visible on-chain. However, this transparency is one of the biggest limiting factors for many real-world applications that require privacy.
TEEs address this challenge by creating a secure environment where smart contracts can process sensitive data while keeping the information private. This enables sophisticated financial applications like private lending protocols where the terms of a loan and collateral amounts remain private, or enterprise solutions where business logic and details of transactions need protection. The ability to execute smart contracts within TEEs opened new avenues for institutional adoption of blockchain technology because organizations can now leverage the benefits of smart contracts while keeping their operations private.
2. Cross-Chain Bridge Security
Cross-chain bridges have emerged as one of the key infrastructures in the blockchain ecosystem, enabling the transfer of assets across different networks. However, these bridges have also been repeatedly targeted by hackers, with hundreds of millions of dollars lost due to security breaches. TEEs offer a strong security solution for cross-chain bridges by providing a secure environment to manage the bridge’s critical operations. When implemented correctly,.
TEEs secure the bridge’s private keys and the validating logic of the bridge from external attacks, even when the host system is compromised. The secure enclave now ensures that cross-chain transactions are being validated according to predetermined rules, and cannot be tampered with by operators in the bridge. This level of security is highly important for those bridges that have to deal with huge volumes since it significantly reduces the risks of unauthorized access or manipulations with the bridge funds. Besides, TEEs allow for atomic swaps between chains with improved security guarantees: cross-chain transactions either complete fully or fail safely, with no possibility of getting the assets stranded or lost.
3. Decentralized Oracle Networks
Oracle networks serve as the crucial link between blockchain networks and external data sources, making them fundamental to many DeFi applications and smart contracts. TEEs have revolutionized Oracle security and reliability by providing a tamper-proof environment for data processing and verification. When Oracle nodes operate within TEEs, the data aggregation and computation processes are protected from manipulation, even by the node operators themselves. This is particularly important for financial data feeds, where even minor tampering could result in significant exploitation of DeFi protocols.
TEEs also enable oracles to handle sensitive data sources while maintaining confidentiality, opening up possibilities for bringing private real-world data on-chain. For instance, an Oracle network using TEEs could securely process private enterprise data or confidential market information without exposing the raw data to node operators or the public blockchain. The attestation capabilities of TEEs also provide strong guarantees that the Oracle network is operating as intended, increasing trust in the system.
Leading Ecosystems and Projects
Secret Network
Secret Network has established itself as a pioneering force in privacy-preserving blockchain technology through its innovative use of Intel SGX. By incorporating TEEs at the protocol level, Secret Network has created a unique platform where privacy isn’t just an add-on feature but a fundamental characteristic of all network operations. The network enables developers to build applications where sensitive data remains encrypted while still allowing for complex computations. This has proven particularly valuable in DeFi applications, where users can trade assets without revealing their positions or strategies. The network’s privacy-preserving smart contracts have enabled innovative applications like secret auctions, where bid amounts remain hidden until the auction concludes, and confidential governance systems where voting remains private while maintaining verifiable results.
Oasis Network
Oasis Network represents a significant advancement in scalable privacy-focused blockchain infrastructure. Their implementation of TEEs goes beyond basic transaction privacy, offering a sophisticated platform for confidential computation at scale. The network’s architecture separates consensus and computation into distinct layers, allowing for parallel processing of private transactions while maintaining strong security guarantees. This design has enabled the development of novel applications in decentralized finance and data tokenization. Financial institutions can leverage the platform to maintain compliance with privacy regulations while participating in DeFi protocols, and enterprises can securely monetize sensitive data sets without exposing the underlying information.
Phala Network
Phala Network has taken a unique approach to implementing TEEs in Web3 by creating a decentralized cloud computing platform that maintains confidentiality guarantees. Their infrastructure enables secure off-chain computation while maintaining the trustless properties of blockchain systems. This has opened up new possibilities for computationally intensive applications that require privacy, such as machine learning models operating on sensitive data or complex financial calculations that must remain confidential. The network’s architecture allows for seamless scaling of confidential computing resources while maintaining strong security guarantees through its TEE implementation.[Previous sections remain the same until Real-World Challenges]
Real-World Challenges and Limitations
The implementation of TEEs in Web3 environments faces several significant challenges that need careful consideration and innovative solutions. These challenges span both technical and ecosystem-wide aspects, requiring coordinated efforts from hardware manufacturers, developers, and the broader blockchain community to address effectively.
Technical Challenges
Hardware dependency represents one of the most significant barriers to widespread TEE adoption in Web3. Current implementations primarily rely on specific hardware configurations, most notably Intel SGX or AMD SEV, which limits deployment flexibility and increases implementation costs. This dependency creates potential bottlenecks in scaling TEE-based solutions and can exclude users who don’t have access to compatible hardware.
Performance overhead is another crucial technical challenge that TEE implementations must navigate. The very mechanisms that ensure security – isolation and encryption – introduce computational overhead that can impact transaction processing speeds and overall system performance. This becomes particularly apparent in high-throughput applications like DeFi protocols, where even small latency increases can significantly affect user experience and market efficiency.
Memory limitations present a significant constraint for complex applications running within TEEs. The secure enclaves typically have restricted memory capacity, which can limit the complexity of operations that can be performed within the trusted environment. This becomes particularly challenging when dealing with data-intensive applications or complex smart contract executions that require substantial memory resources.
Side-channel attacks pose a sophisticated threat to TEE security. Despite the robust protection mechanisms, researchers have identified various potential attack vectors that could exploit hardware vulnerabilities or timing differences in TEE operations. These attacks, while complex to execute, demonstrate the need for continuous security improvements and careful implementation practices.
Ecosystem Challenges
Standardization, or rather the lack thereof, presents a significant hurdle in the TEE ecosystem. The absence of common standards across different TEE implementations makes it difficult for developers to create portable applications and for projects to ensure interoperability. This fragmentation can lead to increased development costs and potential security risks as teams navigate different implementation requirements and security models.
Integration complexity remains a significant barrier to adoption. Incorporating TEEs into existing blockchain infrastructure requires substantial engineering effort and expertise. Teams must carefully design their architecture to maintain security guarantees while ensuring efficient interaction between TEE and non-TEE components. This complexity can extend development timelines and increase project costs.
The developer experience around TEE implementation presents its own set of challenges. Building applications for TEE environments require specialized knowledge that many blockchain developers may not possess. The learning curve is steep, and the available development tools and debugging capabilities are often less mature than those available for traditional blockchain development.
Cost considerations extend beyond just hardware requirements. Operating and maintaining TEE-based systems involves ongoing expenses related to specialized hardware, increased computational overhead, and the need for expertise in both TEE and blockchain technologies. These costs can be particularly challenging for smaller projects or startups looking to implement privacy-preserving solutions.
Best Practices for Implementation
Security Considerations
Security in TEE implementations requires a comprehensive approach that goes beyond just utilizing the hardware capabilities. Regular firmware and software updates are crucial, as they address newly discovered vulnerabilities and improve system performance. However, updates must be carefully managed to ensure they don’t introduce new vulnerabilities or disrupt existing operations.
Attestation mechanisms form the backbone of TEE security and must be robustly implemented. This involves creating reliable protocols for verifying the authenticity of TEE environments and ensuring that only authorized code executes within the secure enclave. The attestation process should be continuous and integrated into the system’s regular operation cycles.
Side-channel attack prevention requires a multi-faceted approach combining hardware features, software design patterns, and operational security measures. This includes implementing timing attack mitigations, managing memory access patterns, and regularly assessing system security against known attack vectors.
Secure key management represents a critical aspect of TEE security. This involves not just the secure generation and storage of keys within the TEE but also careful management of key rotation, backup procedures, and access controls. A comprehensive key management strategy must account for both routine operations and emergency scenarios.
Development Guidelines
Successful TEE implementation begins with a careful architecture design that minimizes the trusted computing base (TCB). This means critically evaluating what code and data must run within the TEE and what can safely operate outside it. A smaller TCB not only improves security but also reduces the complexity of security audits and system maintenance.
Error handling in TEE environments requires special attention due to the sensitive nature of operations. Developers must implement comprehensive error-handling mechanisms that maintain security guarantees even in failure scenarios. This includes secure error logging that doesn’t leak sensitive information and graceful degradation paths that maintain system security.
Communication between TEE and non-TEE components must be carefully designed and implemented. This includes establishing secure channels for data transfer, implementing proper authentication mechanisms, and ensuring that the communication protocols themselves don’t introduce vulnerabilities. Encryption of all sensitive data in transit is essential, as is validation of data integrity at both ends of the communication channel.
Regular security audits play a crucial role in maintaining TEE system security. These audits should examine not just the TEE implementation itself but also the surrounding system components and interaction points. Audit procedures should be established early in the development process and maintained throughout the system’s lifecycle.
Future Prospects and Innovations
The future of TEEs in Web3 looks promising, with several emerging trends:
Technical Innovations
- Hardware Improvements: New generations of TEE hardware with enhanced security and performance
- Cross-Platform Solutions: Development of platform-agnostic TEE implementations
- Improved Developer Tools: Better development frameworks and debugging capabilities
- Enhanced Scalability: Solutions for handling larger datasets and complex computations
Ecosystem Development
- Standardization Efforts: Industry-wide initiatives for TEE interoperability
- Integration Frameworks: Simplified integration paths for existing blockchain projects
- Privacy-Preserving DeFi: New financial protocols leveraging TEE capabilities
- Cross-Chain Solutions: Enhanced security for blockchain bridges and interoperability protocols
Conclusion
Trusted Execution Environments represent a crucial technology for advancing privacy and security in Web3. While challenges exist, the continuous innovation and growing ecosystem support suggest a bright future for TEE applications in blockchain technology. As the technology matures and becomes more accessible, we expect increasingly sophisticated applications that leverage TEEs to enable truly private and secure decentralized systems.
For developers and organizations looking to implement TEE solutions, it’s essential to carefully evaluate the specific requirements of their use case, consider the available technologies and their limitations, and follow best practices for secure implementation. The journey toward widespread TEE adoption in Web3 is ongoing, but the foundation for a more private and secure decentralized future is being laid today.
